Make browser or API call requests via Rust script can be done with Reqwest module. It’s easier than using Hyper, which recently has a lot of changes. There nothing many articles, guidelines or working examples with the latest version of Hyper and Reqwest for advanced usage.
Several things that I want to achieve here where there lack of coverage on:
- How to enable reqwest working with proxy
- How to use Authorization Beaver in reqwest
- How to applied self signed certificate
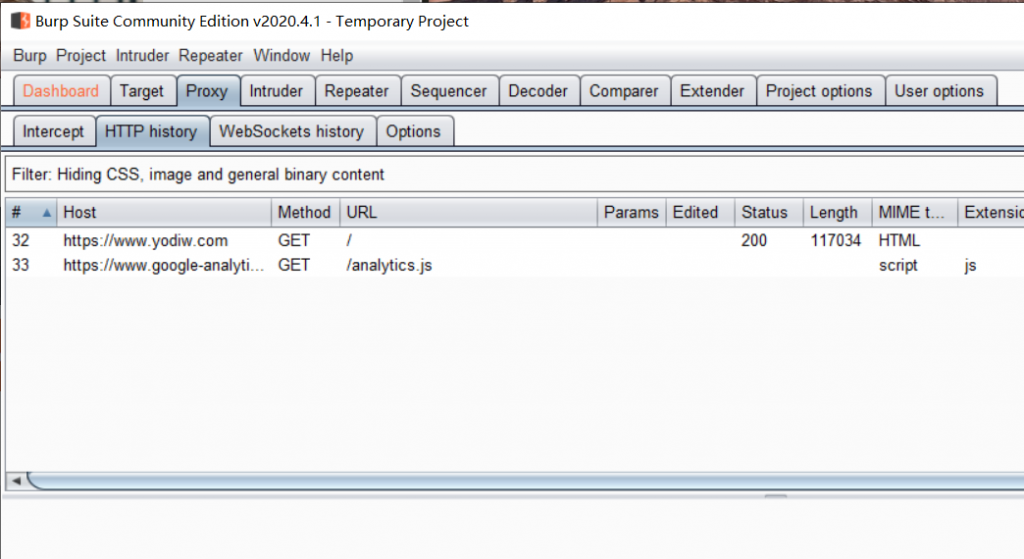
- How to capture the traffic via Burp for monitoring
I tried with Hyper and Hyper Proxy, but it seems it’s more complicated and harder to do than Reqwest.
Here is an step by step to enable proxy, certification and captured by Burp.
cargo.toml
[dependencies]
hyper = "0.13.5"
hyper-native-tls = "0.3.0"
reqwest = { version = "0.10.4", features = ["blocking", "json", "gzip"] }
tokio = { version = "0.2", features = ["full"] }
diesel = { version = "1.4.4", features = ["postgres", "chrono"] }
dotenv = "0.15.0"
chrono = { version = "0.4.11", features = ["serde"] }
serde = { version = "1.0.110", features = ["derive"] }